Why DNS Encryption Became Essential
Every time you type a website address into your browser, your device asks a simple but revealing question: “Where can I find this domain?” Traditionally, this request — known as a DNS (Domain Name System) query — travels across the internet in plain text. It’s like sending postcards instead of sealed letters; anyone between you and your destination can read or alter them. Internet Service Providers (ISPs), network administrators, or even malicious attackers could monitor or manipulate these unprotected DNS requests.
This lack of privacy became a growing concern as data protection and online surveillance entered public debate. As encryption spread across email, messaging, and web traffic, DNS remained a glaring exception — the first step of every online interaction was still exposed. This vulnerability sparked the evolution of encrypted DNS protocols: methods that secure DNS queries so they cannot be easily tracked, intercepted, or tampered with.
Among the leading solutions are three major contenders: DNS over HTTPS (DoH), DNS over TLS (DoT), and DNSCrypt. Each approaches the challenge differently, balancing privacy, performance, and compatibility. Understanding these distinctions reveals much about the future of internet security — and the invisible mechanics that protect your online experience.
From Plaintext to Privacy: The Evolution of DNS
The DNS system is often described as the “phonebook of the internet.” When you visit a website like example.com, your device queries a DNS server to find the numerical IP address of that domain. However, traditional DNS operates over UDP or TCP on port 53 — without encryption.
This design worked fine in the 1980s when the internet was small and trust was implicit. But today, this openness poses risks: ISPs can log browsing behavior, governments can filter or block domains, and attackers can perform man-in-the-middle or DNS spoofing attacks to redirect traffic.
Efforts like DNSSEC (DNS Security Extensions) introduced data integrity verification through digital signatures, ensuring responses weren’t forged. Yet DNSSEC didn’t hide the content of queries — it protected accuracy, not privacy. That gap gave rise to encrypted DNS, which conceals not only the response but also the request itself.
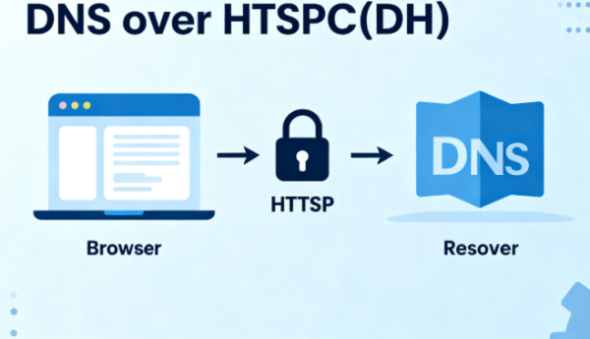
Understanding DNS over HTTPS (DoH)
DNS over HTTPS (DoH) encapsulates DNS queries within standard HTTPS traffic, using port 443 — the same port your browser uses for secure web pages. This makes DoH requests indistinguishable from normal web traffic.
Because DoH blends seamlessly with regular HTTPS connections, it’s nearly impossible for ISPs or censors to differentiate DNS traffic from any other encrypted data. This property offers strong resistance against content blocking and traffic analysis.
Browsers like Mozilla Firefox, Google Chrome, and Microsoft Edge have integrated DoH directly into their settings, allowing users to choose resolvers such as Cloudflare, Google Public DNS, or NextDNS. By tunneling DNS requests through HTTPS, DoH offers convenience and privacy without requiring special system configuration.
However, DoH’s integration at the application level (rather than the operating system level) means each browser or app may manage DNS independently. This can bypass local parental controls or enterprise network monitoring — a source of tension between privacy advocates and network administrators. While DoH is ideal for individuals seeking to avoid surveillance, organizations may find it disrupts network policies or compliance frameworks.
Understanding DNS over TLS (DoT)
DNS over TLS (DoT) takes a slightly different approach. Instead of embedding DNS traffic within HTTPS, it secures it with Transport Layer Security (TLS) — the same cryptographic foundation used for HTTPS — but on a dedicated port (853).
DoT operates at the system or network level, meaning it can encrypt all DNS queries from any application on a device. This makes it easier for network administrators to monitor, route, or control DNS behavior while maintaining user privacy.
Android, for instance, supports DoT natively through its “Private DNS” setting, allowing users to connect to trusted resolvers such as Cloudflare, Quad9, or AdGuard. Many modern routers and firewalls also support DoT, making it suitable for home or enterprise environments.
DoT’s separation from regular HTTPS traffic simplifies network troubleshooting and policy enforcement. Yet, that same transparency can also expose it to censorship — since port 853 traffic can be easily identified and blocked. While DoT is efficient and cleaner in architecture, it’s less stealthy than DoH in restrictive networks.
Understanding DNSCrypt
Before DoH and DoT became standardized by the IETF, DNSCrypt emerged as an independent, open-source project aimed at encrypting DNS traffic. It authenticates communication between a user’s device and the DNS resolver using modern cryptographic signatures.
DNSCrypt doesn’t rely on TLS or HTTPS; instead, it employs its own encryption and authentication mechanisms. This independence means it avoids the complexity of certificate management and can sometimes offer faster performance with lower overhead.
Despite its technical elegance, DNSCrypt never gained universal adoption because it isn’t an official internet standard. Major operating systems and browsers didn’t integrate it by default, limiting its mainstream appeal. Nevertheless, privacy enthusiasts and advanced users still value DNSCrypt for its flexibility, speed, and resistance to centralization — since it often supports smaller, independent resolvers rather than large corporations.
Privacy, Performance, and Compatibility: The Core Trade-offs
Encrypted DNS protocols all serve the same purpose — protecting the confidentiality of your DNS traffic — but each has unique trade-offs across three dimensions: privacy, performance, and compatibility.
Privacy:
DoH provides the strongest privacy cloaking because it hides DNS traffic inside normal HTTPS streams, making it nearly invisible to network-level surveillance. However, its reliance on centralized providers (like Google or Cloudflare) means you’re shifting trust rather than eliminating it. DoT offers transparency and security but can be filtered more easily. DNSCrypt excels at decentralization but requires manual setup.
Performance:
DoT typically performs best because it’s lightweight and runs directly over TLS. DoH can introduce slightly more latency due to the overhead of HTTPS sessions, especially in mobile networks. DNSCrypt’s performance depends on implementation — it can be fast but lacks the widespread optimization that DoH and DoT enjoy from major service providers.
Compatibility:
DoH integrates smoothly with browsers, DoT works well system-wide, and DNSCrypt fits niche setups. Compatibility often determines which protocol users adopt — casual users prefer DoH in browsers, while advanced users or network managers rely on DoT.
The Centralization Debate: Privacy vs. Power
As DoH and DoT gain adoption, a new question arises: Who controls the encrypted DNS infrastructure?
When browsers like Firefox or Chrome automatically route DNS queries through specific third-party resolvers, it concentrates power in a few hands. For example, Google Public DNS and Cloudflare handle vast volumes of encrypted DNS traffic. While these providers promise not to log personal data, centralization creates single points of trust — and potential surveillance chokepoints.
Privacy advocates argue for decentralization: the ability for users to choose from many independent resolvers. Projects like DNSCrypt and decentralized resolver lists aim to maintain diversity in the DNS ecosystem, ensuring that no single entity can dominate DNS privacy infrastructure.
On the other hand, large providers bring reliability, DDoS resistance, and speed that small servers can’t match. This tension between privacy and practicality mirrors the broader internet debate — convenience versus control.
Adoption Trends and Global Growth
Recent research shows rapid growth in encrypted DNS adoption worldwide. According to academic studies and measurements by APNIC and Mozilla, DoH adoption surged after 2019, largely driven by browser integrations. DoT, meanwhile, expanded through Android and router-level support.
Enterprises are slowly embracing encrypted DNS but often struggle with visibility — once DNS queries are encrypted, traditional firewalls and proxies lose insight into which domains employees are accessing. Some organizations deploy internal DoT resolvers or DNS logging proxies to regain observability while maintaining encryption.
Global DNS providers like Cloudflare (1.1.1.1), Quad9 (9.9.9.9), and Google Public DNS (8.8.8.8) now support both DoH and DoT, giving users flexibility to choose their preferred protocol. Smaller privacy-focused services, such as AdGuard DNS and NextDNS, extend these features with content filtering and analytics.
Performance Testing: Which One Is Faster?
Independent benchmarks suggest performance differences are small but measurable.
- DoT often shows the lowest latency under stable conditions — typically adding less than 10 ms overhead compared to plain DNS.
- DoH can be marginally slower due to HTTPS handshakes and multiplexing overhead, but persistent connections mitigate much of this delay.
- DNSCrypt can be faster in lightweight environments, though results vary depending on resolver location and implementation.
In real-world usage, the difference is almost imperceptible to users. What matters more is the reliability of the resolver and the stability of the connection. For users prioritizing speed, selecting a geographically close resolver often improves performance more than the choice of protocol itself.
Security Beyond Encryption
While encrypted DNS hides queries from intermediaries, it doesn’t solve all privacy problems. Once your DNS resolver knows which domains you query, it can still log or analyze that data. Encryption protects in transit, but trust must still exist at the endpoint.
Some services, like Quad9, strengthen protection by integrating threat intelligence, blocking domains known for malware or phishing. Others, such as AdGuard DNS, allow custom filters or parental controls.
Users should view encrypted DNS as one layer in a broader privacy toolkit — alongside VPNs, HTTPS, and endpoint security. Without complementary measures, encrypted DNS alone cannot guarantee full anonymity.
How to Enable Encrypted DNS
Most users can enable encrypted DNS easily today:
- In browsers: Firefox → Settings → Privacy & Security → Enable “Use DNS over HTTPS.” Chrome → chrome://settings/security → “Use secure DNS.”
- In Android: Settings → Network → Private DNS → Choose “dns.google” or “1dot1dot1dot1.cloudflare-dns.com.”
- On routers or PCs: Configure DoT or DNSCrypt manually, depending on firmware support.
Many resolvers provide both DoH and DoT endpoints, allowing users to mix convenience with system-level privacy. For instance, Cloudflare supports DoH via https://1.1.1.1/dns-query and DoT via tls://1.1.1.1.
The Future: DoQ and Beyond
As internet protocols evolve, newer standards such as DNS over QUIC (DoQ) are emerging. Built on the QUIC transport protocol (used in HTTP/3), DoQ promises faster handshakes, improved connection reliability, and better multiplexing.
DoQ combines the best of both worlds: the stealth of DoH with the efficiency of DoT. Although still early in deployment, it represents the next phase of encrypted DNS — one that adapts to the modern, latency-sensitive internet.
Why Encrypted DNS Matters for Everyone
Encrypted DNS may sound like a niche concern for cybersecurity professionals, but it affects anyone who values privacy, speed, and reliability online. Every digital action — searching, streaming, shopping — starts with a DNS query. Securing that first step prevents data leakage, censorship, and targeted advertising based on browsing patterns.
For users in restrictive regions, encrypted DNS can bypass censorship without needing a full VPN. For enterprises, it helps secure communications across distributed workforces. And for the broader internet, it represents a movement toward a more private, user-respecting digital ecosystem.
Conclusion: Choosing the Right Protocol
So, which encrypted DNS protocol is best? It depends on your priorities.
- If you value stealth and privacy above all, DoH is ideal — it blends invisibly with web traffic.
- If you prefer stability and system-wide encryption, DoT offers robust security with simpler network management.
- If you want independence and decentralization, DNSCrypt remains a powerful choice for advanced users.
Each represents a step toward a safer, more private internet — sealing the postcards of yesterday inside the envelopes of tomorrow.
As the internet continues its shift toward end-to-end encryption, DNS will no longer be the weak link in privacy. Whether through DoH, DoT, or DNSCrypt, encrypted DNS has transformed from a niche experiment into a cornerstone of digital freedom.