In today’s digital world, passwords remain the cornerstone of online security. Yet, despite widespread awareness, many users continue to rely on weak or reused passwords, exposing themselves and their organizations to a significant risk of account compromise. From identity theft to financial loss, the consequences of weak passwords can be severe. This comprehensive guide will explore the best practices for creating strong passwords, combining expert recommendations, practical strategies, and the latest research in cybersecurity.
Understanding the Fundamentals of Password Security
Before diving into practical strategies, it is essential to understand what constitutes a strong password. A strong password is more than just a random combination of characters. It is resilient against various attack methods, including brute-force attacks, dictionary attacks, and social engineering. Here are the core principles:
- Length Over Complexity
While many people focus on including symbols, numbers, and mixed-case letters, modern security standards emphasize length as the most critical factor. Passwords of 12–16 characters or more are generally considered strong. - Diversity of Characters
A strong password should combine uppercase letters, lowercase letters, numbers, and symbols. However, complexity alone is insufficient if the password is short or predictable. - Avoiding Predictable Patterns
Common sequences like “123456”, “password”, or “qwerty” are extremely vulnerable. Even adding a symbol at the end, such as “Password1!”, does not offer adequate protection. - Uniqueness Across Accounts
Reusing passwords across multiple accounts is one of the most dangerous practices. A breach in one service can compromise every account using the same credentials.
Common Threats to Password Security
Understanding the types of attacks helps clarify why strong passwords are essential:
- Brute-force attacks systematically try every possible combination until the correct password is found. Longer passwords drastically increase the time required for such attacks.
- Dictionary attacks use lists of common words and phrases to guess passwords. Combining unrelated words or using nonsensical phrases can mitigate this risk.
- Social engineering exploits human behavior rather than technology. Phishing emails or manipulated support calls can trick users into revealing passwords, emphasizing the need for security awareness.
Best Practices for Creating Strong Passwords
Creating strong passwords requires a balance between security and memorability. The following strategies are widely recommended by cybersecurity experts:
Prioritize Length Over Complexity
A 16-character password using common words can be stronger than an 8-character complex password. For example:
- Weaker: P@ssw0rd!
- Stronger: BrightTiger$Moon42
Use Randomly Generated Passwords
Random passwords are virtually impossible to guess. Password managers can generate secure, high-entropy passwords automatically. For example:
xT7$gB!2pL@9wQ8m
Employ Memorable Strategies
Not all passwords need to be purely random. Strategies like these can help:
- Acronyms from Phrases: Take the first letters from a sentence. For instance, “I love reading books every night!” becomes
ILRBE!2025. - Unrelated Word Combinations: Combine random words with numbers and symbols, e.g.,
BlueTiger$Moon42. - Personal Patterns Without Personal Info: Avoid birthdays, names, or phone numbers, but create a personal mnemonic or story.
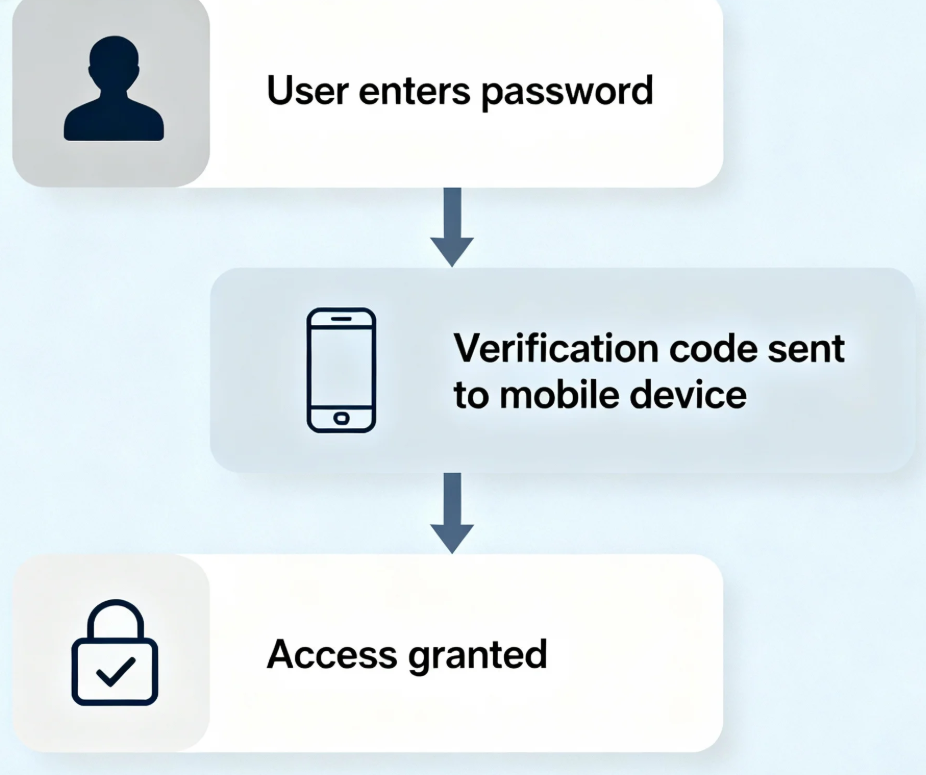
Implement Multi-Factor Authentication (MFA)
Passwords are often the first line of defense, but they should not stand alone. MFA provides an additional verification step using:
- Mobile codes (SMS or authenticator apps)
- Biometric authentication (fingerprints or facial recognition)
- Hardware tokens (e.g., YubiKey)
Even if a password is compromised, MFA can prevent unauthorized access.
Advanced Password Management Techniques
Strong passwords are useless if they are mismanaged. Effective strategies include:
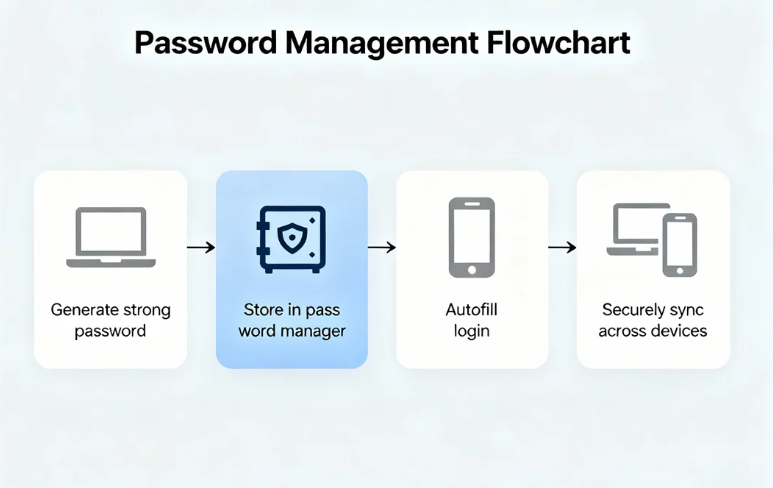
Use a Password Manager
Password managers store and encrypt passwords, enabling users to maintain unique credentials across multiple platforms. Key benefits include:
- Auto-generation of secure passwords
- Secure storage with encryption
- Autofill and convenience, reducing password fatigue
Popular password managers include 1Password, Bitwarden, and LastPass.
Regularly Update Critical Passwords
Not every password needs frequent change, but sensitive accounts (banking, email, cloud storage) should be updated periodically. This reduces exposure if a breach occurs without immediate detection.
Monitor for Breaches
Tools like Have I Been Pwned allow users to check if their email or passwords have been exposed in breaches. Proactively changing compromised credentials is crucial.
Organizational Perspective: Implementing Strong Password Policies
For enterprises, password management extends beyond individual habits. Challenges include employee compliance, training, and technology integration. Effective organizational strategies include:
- Single Sign-On (SSO): Reduces the number of passwords employees need to manage.
- Mandatory MFA: Critical for sensitive internal systems.
- Regular Employee Training: Employees should understand phishing, social engineering, and the importance of unique passwords.
- Policy Enforcement: Automated rules for password complexity, expiration, and reuse prevention.
Common Questions About Strong Passwords
Q: Are complex passwords always necessary?
A: Complexity helps, but length and uniqueness are more critical. A 16-character passphrase can outperform a short, complex password.
Q: Can passwords be both strong and memorable?
A: Yes. Using mnemonics, random word combinations, and acronyms allows users to recall passwords without compromising security.
Q: Is a password manager safe?
A: When using reputable password managers with strong encryption and MFA, yes. They significantly enhance security by enabling unique passwords for all accounts.
Visualizing Password Security
- Password Strength Chart: A visual scale from weak (e.g.,
123456) to very strong (e.g.,BrightTiger$Moon42). - MFA Workflow Diagram: Demonstrates how an additional verification step prevents unauthorized access.
- Password Breach Flow: Illustrates how reused passwords across platforms can lead to multiple account compromises.
Building a Culture of Strong Passwords
Strong passwords remain a cornerstone of personal and organizational security. While creating long, random passwords is ideal, practical strategies such as mnemonics, password managers, and multi-factor authentication make it feasible for anyone. By understanding risks, applying best practices, and leveraging technology, users can significantly reduce the likelihood of account compromise.
Actionable Takeaway:
“Every account deserves a unique, long password—managed securely with a password manager and protected with MFA.”
Adopting these strategies not only secures individual accounts but also contributes to a safer digital ecosystem for everyone.


